D-Network
D-Network facilitates protected and completely transparent e-mail messaging between organizations that have joined the D-Network service network. Data protection takes place at the "Company-Confidential" level without user action. Also the address information of both parties stay protected.
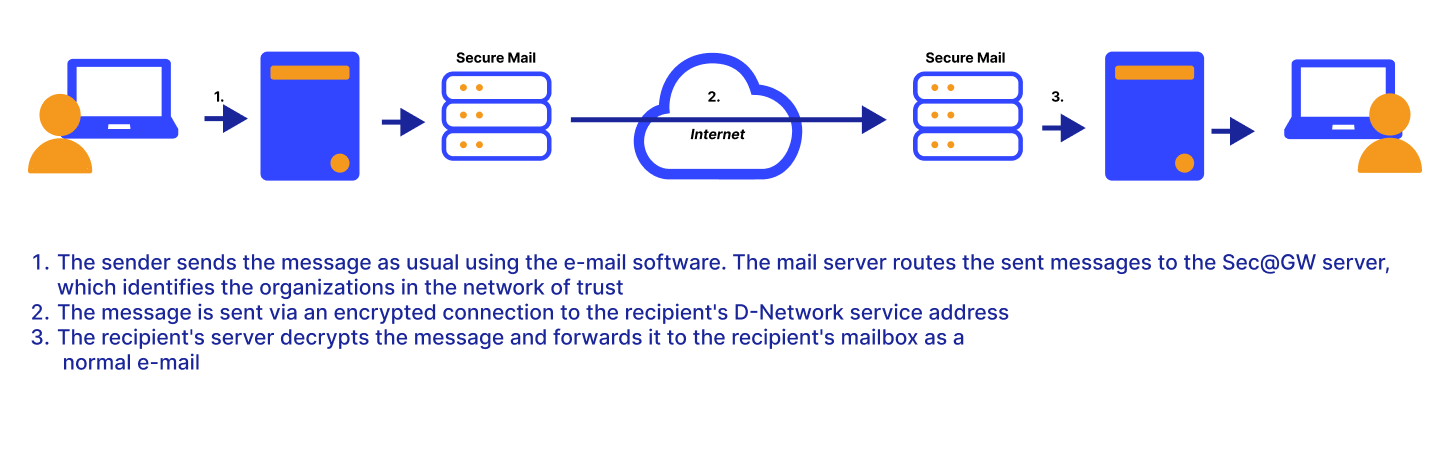
Example of D-Network operation in practice
Data transfer takes place directly between the parties' D-Network applications without proxies using a secure TLSbased transfer method.
The received message can be treated as a normal e-mail in the receiver's e-mail server.
- Data transfer in D-Network: When a message is marked to be sent using D-Network, first the receiver's domain is matched against information in the access rights database. If sending is allowed, the message is protected and a secured connection to receiver network is created. Information regarding session and identifier is sent over the protected connection so that receiving server can confirm that sending server has a right to send messages. If the sender has a right to send messages, the receiving server sends its own corresponding data as a reply, after which message is sent over the protected connection. In case
the sending of message fails or is interrupted, an attempt to resend the message will be made for predefined amount of times after a pause. If resending fails after configured resend time message is sent using the next authentication level in line from encryption control rules.
- D-Network Destination Manager: It is possible to add custom D-Network destination servers. The destination servers must be Secure Email servers with D-Network capabilities. Servers belonging to the official D-Network distribution do not need to add other servers in the official distribution.
The System administrator can request that the organization be registered and added to D-Network from DCenter.

